I did
mention that I am involved in incident response process development, constantly
learning something new in this field. Possible, I presented how that process
can be created basing on the approach introduced by Lockheed Martin. The idea is
to gather as much information as it is possible before any process can be
created. Checking latest researches it seems that there are five stages of
maturity of the Incident Response Process. What can be said, is the fact that
digital crime is getting to be even stronger, and is it hard to still think in this
linear way. We need to develop new methodologies and choose how to react when
the alarm raise. For years, researches and IT investigators have been
developing new phases of investigation models and approaches. I think that all
sub-processes such as forensics investigation, APT response, and basically intrusion
detection must be very closely combined together, and together create incident
response process. On the other hand that process should be constantly developed
to fit and adapt to changing threats and new technologies. Another problem
could be the amount of false-positives and sophisticated attacks. But, at the same time when the crimes scene is
becoming more and more ‘digital’ and switching its place from streets into the ‘net’,
the need for digital investigation appeared. Incident response process should
answer questions how to behave and what to do when security controls reports policy
violations or breaches. Computer forensics investigation should perfectly fit
into the process and have an opportunity to develop. The clue is, how to check
if the incident is legitimate, and how to prove the relevance of evidence
collected on the digital crime scene? Without the process of verification and
forensics approach to the alarms no incident
response process would exist. I would like to present how the process of
forensics investigation looks like and hopefully describe how it is applied
into incident response process.
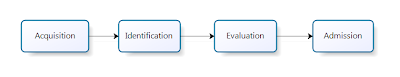
All of
above and much more have been thought years ago, when the FBI Laboratory
presented the very first model of computer forensics investigation. It was in 1984 when Pollitt introduced
Computer Forensic Investigative Process.
 |
| Computer Forensic Investigative Process |
In the first
phase, the investigator was asked to collect evidence – in forensically sound manner of course – identify components in the
evidence and transform them to be human-readable. Then analyst checked if any
identified components represented a legitimate evidence. This happened in
Evaluation phase. At the end of this process all collected evidence were
presented in the court of law. I suppose that this model can be freely used at
the beginning of any process creation. We have preparation, analysis and
outputs. Possibly applied into SIPOC
thesis. Then, many years passed and many other models have been presented.
Awesome job in this field was done by Carrier and Spafford, who presented IDIP (integrated
digital investigation process). I think that IDIP was the very first mature
models in this field. Carrier also introduced the definition of ‘digital crime
scene’ . They described the pre-preparation phases, in which appropriate
personnel training and tools should be prepared. What is more, they also
strongly marked the importance of security controls and detection process.
Another awesome hint, in IDIP model we can find sub-processes and, division
into technical and non-technical data acquisition. This version was upgraded
several years after and named EDIP.
Great work
was done by the team Yunus Yusoff, Roslan Ismail and Zainnuddin Hassan. They were
basing of other investigation modes, and grouped together some similarities of
all methods and methodologies. They proposed generic investigation process –
known as GCFIM (Generic Computer Forensic Investigation Model).
 |
| Generic Computer Forensic Investigation Model |
I would
like to shortly described phases in this model. The first one is obvious, appropriate preparation must be taken into consideration
before any other sub-process could take place. Tools and personnel should be
trained and checked. Additional steps must be taken from management authorities
to support CSIRT during investigation process (privileges, access, approvals). The
second step – Acquisition and Preservation – steps contain sub-processes such
as: identifying, collection, transporting, storing and preserving evidence(
simply collect and prepare data for further analysis). The stages analysis and
presentation are easily understood phases and naturally can be divided into more
detailed sub- processes. The last stage is all about mitigation, resolution and
reporting. At the graph we can notice
some kind of ‘sequence’, but what is more, there is a possibility that we can
move backward during investigation and having ability to ask questions one more
time.
The GCFIM
model is a perfect generic model, that any CSIRT and forensics investigators
can start with when creating own incident response processes. It seems that the
main stream or flow of this model can be easily recognizable in incident
response processes – which contains forensics investigation also. Some kind of similarity between these two
models is appearing. One of them should
be very general and apply specifically to all incidents (in physical world),
where particular policies and people need to be engaged, and the second one
more detailed and sophisticated taking place in digital crime scene.
Brak komentarzy:
Prześlij komentarz